Gateways & Routing
ISP
Virgin Media Fiber 1Gbit/s down / 100Mbit/s up.
Worst connection ever: MTU: 1468, no IPv4, no router bridge mode.
Two gateways
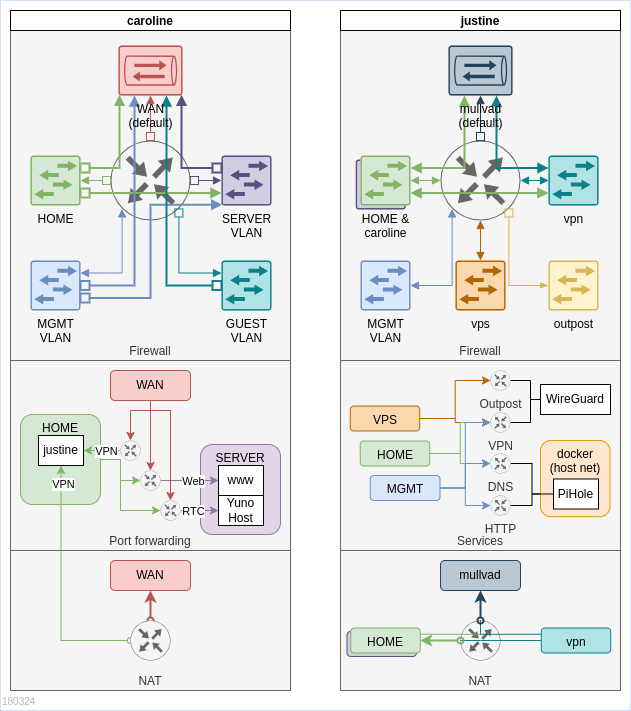
There are two gateways on the network:
- caroline - exposed to the internet, provides access to internet and forwards connections to servers in SERVER VLAN
- justine - VPN G/W that connects to Mullvad and terminates incoming WireGuard VPN connections
Clients use caroline as G/W for direct internet access and justine as G/W for Mullvad protected internet access. Additionally caroline runs DNS server that uses the ISP DNS server, while justine will use PiHole and Mullvad's DNS server.
Routing with two gateways
Things get very complicated with two gateways setup. Clients need to be able to direct traffic to correct gateway in response to connections coming from one or the other gateway.
Gateway forwarded connections:
- caroline forwards from the internet to access internal network to:
- public SERVER network services from outside: blog, younohost etc.
- justine WireGuard VPN
- justine forwards from internet VPN connected devices to:
- HOME network
- to caroline for SERVER network
This creates the challenge where devices can be configured with any G/W and need to be able to forward the traffic to the other G/W in some cases:
- local IP & bridge - VPN clients could be bridged directly and assigned bridged network IP
- NAT - packets coming into the network are MASQUERADE'd to G/W IP address (how it is done currently)
- static route - push static routes to all clients so response to packets coming from G/W terminated IPs (e.g. VPN) are forwarded back to correct G/W
- ICMP redirect - both G/W could be configured to inform clients on the correct G/W to use for packets destination
Problems:
- NAT will obscures the source IP address making troubleshooting, monitoring and accounting more difficult.
- Static routes or redirects will work if G/W can be deduced from destination IP address.
- ICMP redirects many not work reliably, will probably drop first packet?
- Pushing routes to clients requires client support, NAT makes things transparent to clients.
Server VLAN
Uses Carolinededicated VM server-gw that uses WireGuard VPN to connect to Vps server. It acts as default G/W sofor outgoingall SERVER VLAN hosts and routes traffic hasout ISPvia Vps over the VPN connection. This way all servers have Vps public IP as their outgoing IP.
Plan:
- traffic
- is
Setforwardedupby Vps over same VPN connection toserver-gwhostandthatfromwillthere- to
SetwwwupforVPNHTTP(S) termination and also toyounohostservice for Jitsi meet streams.Sanbox VM network
Igor runs dedicated network (vnet) with
Vps host that will forward all traffic through it (like Mullvad would) so that public IP is of VpsConfigure DHCP for SERVER VLAN to useserver-sanbox-gwsoforallVMstraffic goes out of Vps
Configure Vpsconnected toforwardit.vpspublictheinternetinternet.with NAT.Don't NAT out tovpsso thatwwwcan see public IPs of clients - it will use default G/W to send replies so they will end up on Vps overvpsVPN throughserver-gw.
ThisThere is neededno sinceport Jitsiforwarding detects public IP automatically and it has to matchinto the domainnetwork. IPThe sonetwork IPis ofisolated Vps.from all other networks.
